Force Protection On Mount
ForceProtectionOnMount is a sandbox setting in Sandboxie Ini (introduced in v1.13.4 / 5.68.4) that forces a file-backed sandbox image to be mounted with root protection enabled. When set, the mount flow and the mount/create dialog enforce the image root protect option so users cannot mount the image without protection.
Usage
When to use
-
You want a sandbox image always mounted in protected mode (prevent unsandboxed processes from accessing the mounted image).
-
Useful for encrypted images where you want to guarantee protection at mount time.
Behavior and UI
-
The General / File Options UI exposes a checkbox bound to
ForceProtectionOnMount(ui.chkForceProtectionin the code).- The checkbox is enabled only when the sandbox is configured as an encrypted sandbox (not for RAM disk).
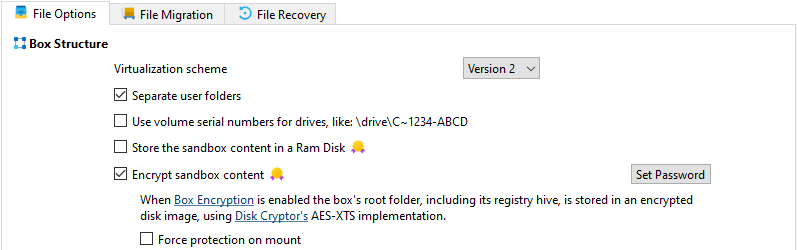
-
When the box image mount dialog is shown programmatically with force applied,
CBoxImageWindow::SetForce(true):- forces
ui.chkProtectchecked, - disables the protect checkbox so users cannot uncheck it,
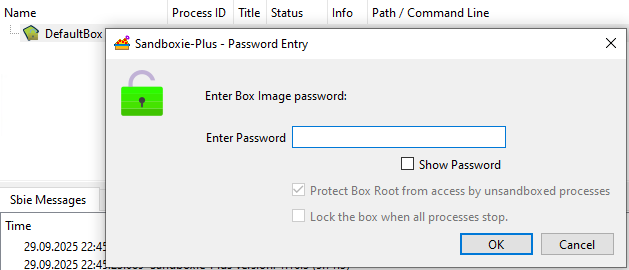
- forces
ui.chkAutoLock(auto-unmount on last process stop) checked/disabled in the dialog. - On mount the service receives a mount request with the
protect_rootflag set; the mount manager and driver enforce protection.
- forces
Technical notes / code references
-
UI reads/writes:
-
Mount wire protocol:
IMBOX_MOUNT_REQcontainsBOOL protect_root;(mount wire header inMountManagerWire.h).2
-
Mount dialog enforcement:
CBoxImageWindow::SetForce(bool force)sets the protect checkbox enabled/checked state.3
-
Mount flow:
MountManager::AcquireBoxRoot(mount manager) will include theprotect_rootflag in mount requests when appropriate.4
-
Start process integration:
Start.cpphandles themount_protectedparameter during sandbox startup and process creation.5
Compatibility & constraints
- Only meaningful for sandboxes using
UseFileImage(file-backed.boximages). - If the filesystem driver or mount manager cannot honor protected mounts (or encrypted containers), mounts may fail and the sandbox will not start - check logs and mount manager errors.
- Protecting the root is enforced at mount time; unmounting while processes run will terminate those processes.
Best practices
- Apply per-sandbox (do not set globally unless you intend to force protection for every sandbox).
Related
UseFileImage- enables file-backed sandbox images.CBoxImageWindow::SetForce- UI enforcement on the mount/create dialog.IMBOX_MOUNT_REQ.protect_root- mount request flag used by the mount manager.StartCommandLine- Command-line operations includingmount_protectedswitch for protected mounting.
-
See UI code in
SandMan\Windows\OptionsGeneral.cpp-COptionsWindow::LoadGeneralandCOptionsWindow::SaveGeneralhandle reading and writing theForceProtectionOnMountkey viam_pBox. ↩↩ -
Mount protocol definition in
..\Sandboxie\core\svc\MountManagerWire.h-tagIMBOX_MOUNT_REQincludes theprotect_rootfield used by the mount manager. ↩ -
Implementation in
SandMan\Windows\BoxImageWindow.cpp-CBoxImageWindow::SetForce(bool force)forces the dialog checkboxes to reflect a forced protected mount. ↩ -
Mount manager code (mount request assembly) will propagate the
protect_rootflag to the service/driver; see the mount manager implementation (e.g.,MountManager::AcquireBoxRoot) in the service codebase. ↩ -
Start process implementation in
Sandboxie\apps\start\Start.cpp- handles themount_protectedparameter during sandbox startup and process initialization. ↩